As Dirk Leopold pointed out in his post, security is one of the most strategically important concerns in the automotive industry in the future. We will be introducing the concepts of security analysis and how they are adressed in a tool, that we have been developing.
A security analysis consists of a number of concepts and their relationships that describe potential threats, security goals, counter measures etc. We have built a tool based on the MPS framework that supports formal capturing of these concepts as well as high customizability for project needs. All the data and concepts shown can be modified and tailored to specific needs.
Basic concepts for a security analysis are "threats" and "attack potential". The "Common Criteria", one of the relevant standards in the field, defines threats as
A threat consists of an adverse action performed by a threat agent on an asset.
and gives the examples of a hacker attacking a system, a worm corrupting something or a system administrator violating privacy. Threats are to be documented and dealt with in the risk analysis.
One important factor in prioritizing threats in countermeasure is the effort that a threat agent would need or, in other words, how much potential an agent has to perform a certain threat. Or, according to the Common Criteria, a "measure of the effort to be expended in attacking a [target of evaluation], expressed in terms of an attacker's expertise, resources and motivation". We like to use the term "Required Attack Potential" (RAP), which indicates how much effort a threat agent must expend to perform a certain threat.
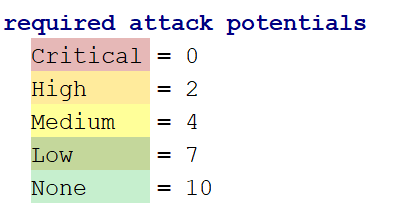
Required Attack Potentials
Since there is no single standard in security analysis, there is some variation on how attack potentials are calculated. Some of these so-called "risk factors" are very common:
- Elapsed Time: How much time is needed / available to perform the threat
- Expertise: How qualified must the threat agent be to perform the threat
- Window of Opportunity: Is the target of evaluation (TOE) easily available to an attacker (e.g., is it a system that is behind closed doors, or is it a car that is driving on the streets)
- Equipment: How complex and elaborate is the equipment needed to perform the attack?
All these are mapped to a certain number is calculated as the some of these factors.
In our tool screenshot below, you can see that the analysis is configured so that we categorize "Expertise" in four levels, from layman to multiple experts. Each level is assigned a value that is being used to calculate the over-all attack potential.
Note that we have a full structured model editor, not just a text file. When we add a new element by pressing return.
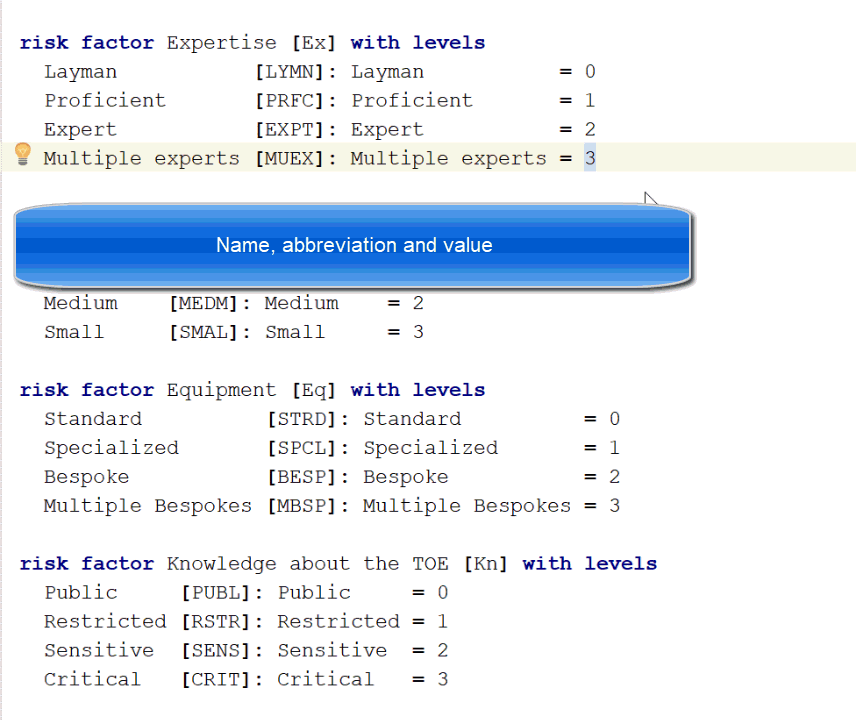
In addition, we define the required attack potentials and their associated values:
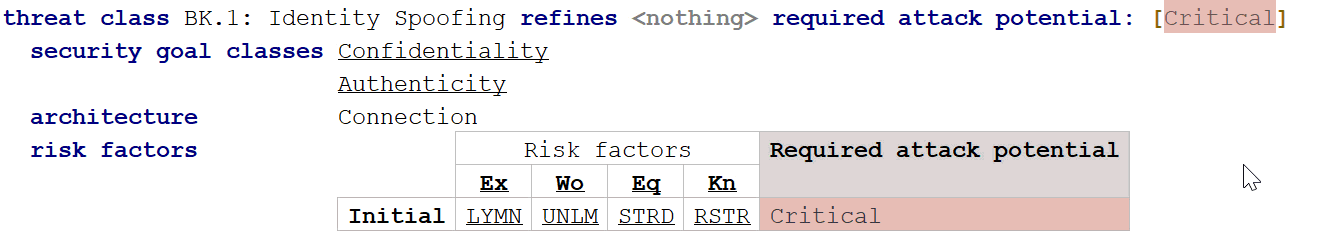
Now we are ready to define our threats. Let's assume we have a system that has no real protection against identity spoofing, so everything would be very simple to attack. So we are setting "Expertise" to "Layman", "Window of Opportunity" to "Unlimited", etc. The sum of the factors is then "0", which results in an attack potential of "critically low".
We can proceed to model further threats. We can toggle between the detailed tree view and an overview. The model can be edited in both representations.
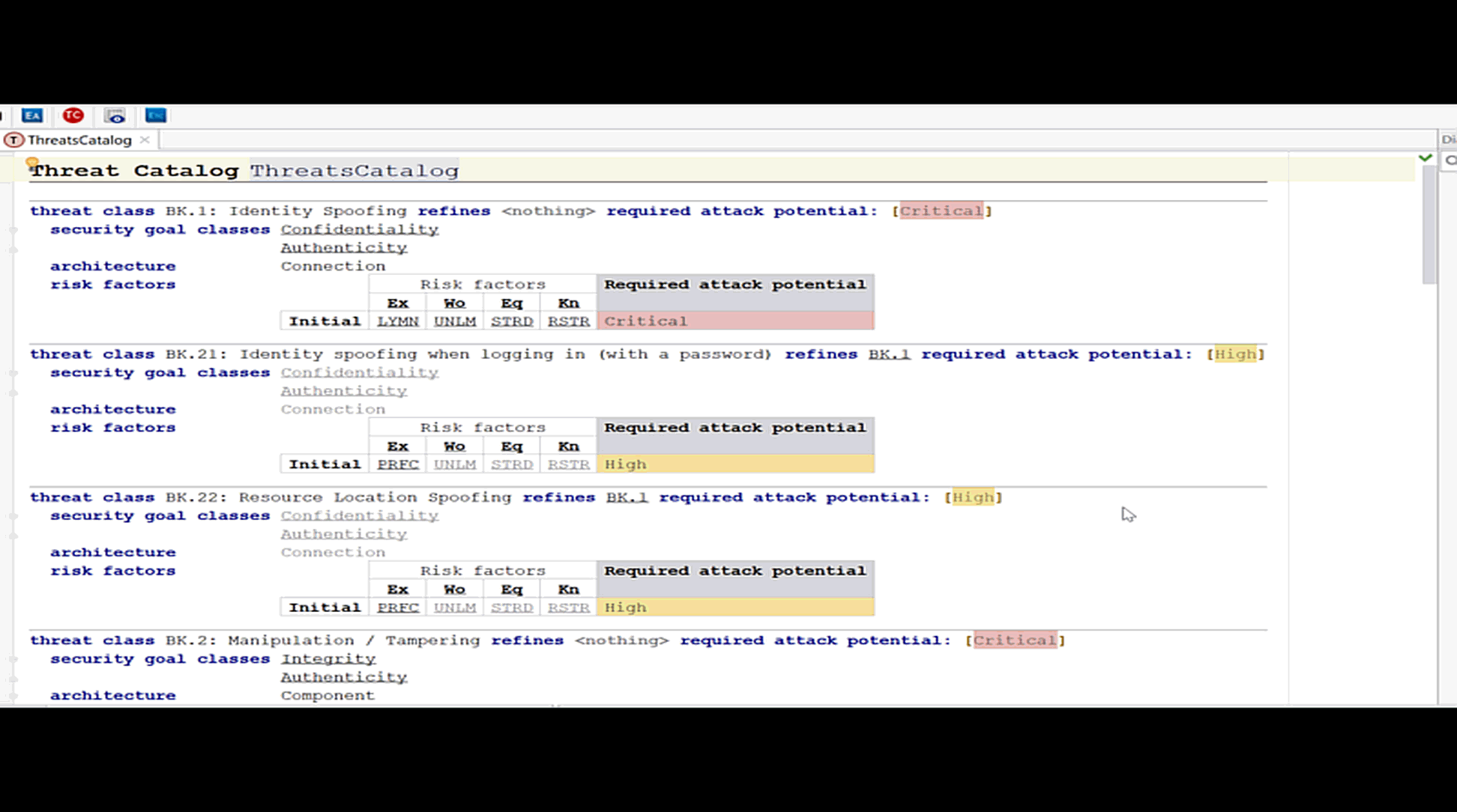
To make an evaluation about the effects of a threat, we also want to model the damage that can be done and combine the information. This will be shown in the next blog post of this series.

Comments