Hardly a week goes by without major security issues being reported. The recently identified vulnerabilities of a wide range of CPUs named “Spectre” and “Meltdown” potentially affect millions of PCs and smartphones. While no actual damage can be connected to these vulnerabilities (yet), it shows that a huge number of users can be affected literally overnight.
Very often vulnerabilities however do get exploited. Ransomware recently caused major harm to private users and companies including the transportation and health sector by rendering their IT equipment useless. Telekom routers have been hacked and disabled. Cars have been successfully compromised and as a result being stolen or manipulated.
In the advent of “smart homes” and self driving cars, this is very worrying.
Who is affected by security threats?
It is difficult to find scenarios – as a private user or as a corporation – were you can safely claim that cyber security is none of your concerns.
PCs, laptops and smartphones are an integral part of may peoples life. New types of devices including smart watches or smart home appliances are entering the mainstream. The vast majority of users in developed countries is “digital and connected”.
In the corporate world, PCs have been around in offices for decades. Today almost all work related activities including the business communication is digital and based on electronic, connected devices. Data can be stolen or tampered with. The availability of services can be compromised.In the area of industrial production the digitalization is advancing too. Smart factories in the era of Industry 4.0 run on software, machines are connected to and communicate with other machines or even the internet.
In order to protect themselves from potential attacks, private citizens and corporations alike have to increase their awareness towards cyber threats and apply suitable measures: make regular backups, use antivirus-software, keep IT-policies and firewalls up to date and have disaster recovery plans in place.
The engineering aspect of safety and security
Products and services available today have been unthinkable only a few decades ago. The Internet, smartphones, 4K television sets and cars with more processing power than Apollo 13. Engineering processes are well established and have resulted in affordable, reliable high-tech products for the masses.
Safety has been an integral part of modern engineering processes for systems comprised of electrical and/or electronic elements for more than 50 years. Functional safety engineering is established across industries. Since the release of IEC 61508 many industry specific norms have followed including ISO 26262 for the automotive sector.
As a result, products have gotten safer and safer over time: Airbags in cars work reliably, highly automated factories provide safe working environments, toaster at home rarely go up in flames any more.
So, if well established engineering processes are able to protects the user’s health and “physical integrity”, why would this be different or more difficult for the “data integrity”?
The ultimate goal in safety is to protect human life. As part of the overall development process, engineers have to ensure that complex electric/electronic systems do not cause harm to the user. In order to achieve that, they have to decompose and understand all functions and their dependencies. Engineers analyze potential failure scenarios and the likelihood of these failures to occur. The negative effects and the probability of the failures are then minimized in the design process. FMEA (Failure Mode and Effects Analysis) and FTA (Fault Tree Analysis) are well established methods being used throughout the safety engineering process.
The principles of any risk management process include the reduction of the risk to an acceptable level by either reducing the likelihood and/or lowering or damage caused by the failure.
For the safety engineering process this translates to making functional failures less likely e.g. by implementing failover mechanisms or using higher quality materials. At the same time the damage potential is lowered e.g. by introducing and improving seat belts in cars.
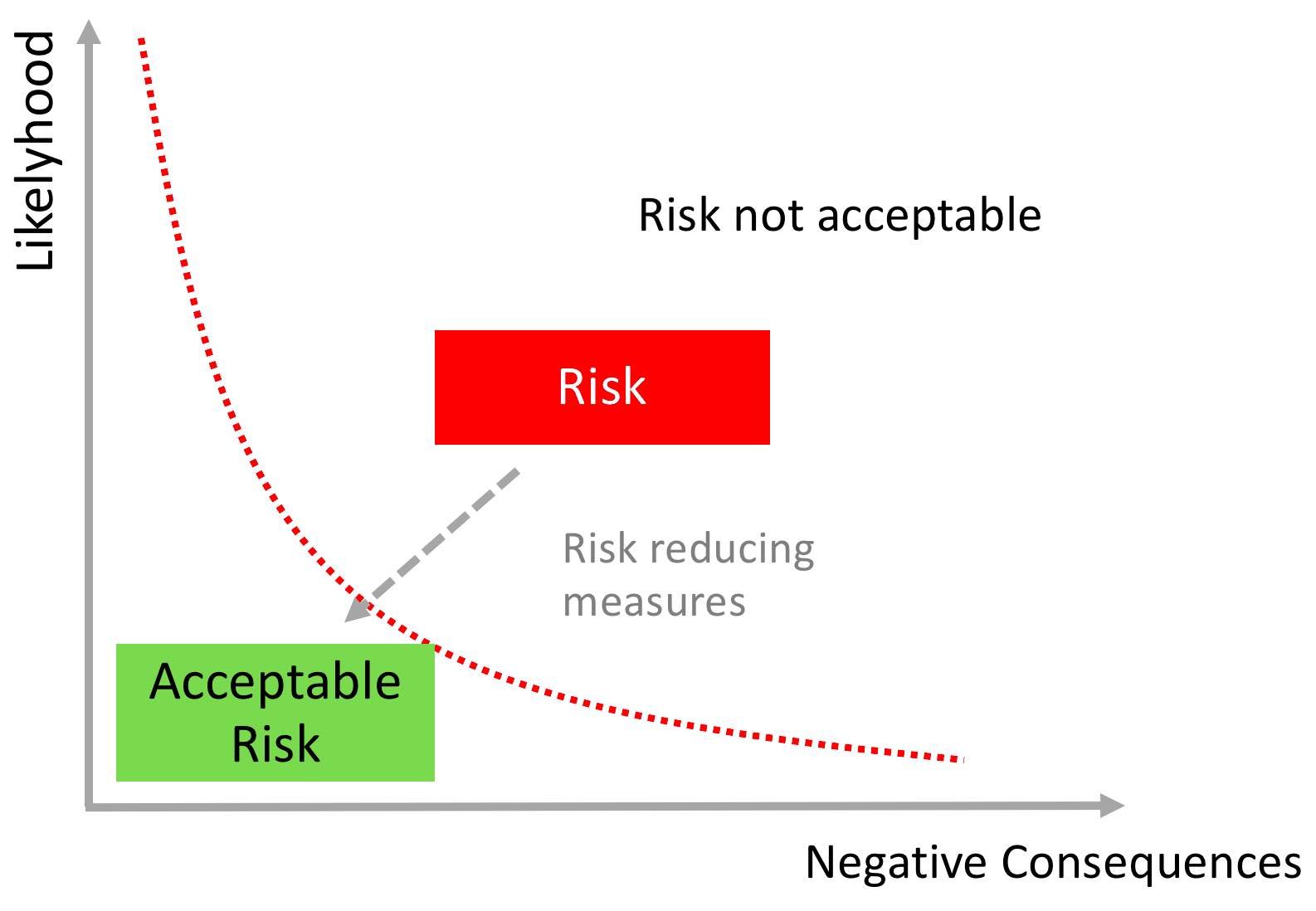
The safety engineering process results in products and services that are not 100% safe - but limit the risk damaging human health to an acceptable level.
A successful security engineering process has to follow a similar approach. The target is to design and implement systems, that limit the security risk to an acceptable level.
The challenges of any security engineering become obvious when we look at the security related parameters of the probability and the negative consequences.
In security engineering we deal with an attacker!
The probability of a security failure to occur can therefore not be determined by statistics. Security vulnerabilities often lead to situations, where a single security failure leads to potentially thousands or millions of attacks in a very short time period.
So, security engineering requires new concepts of estimating the probability of an attack including aspects like the motivation, the experience and the time required by an attacker.
All these aspect are subjective and dynamic as they change over time.
The negative consequences or damages resulting from an attack on security include a wide range. Safety ist still one relevant aspect as a security breach might lead to situation that can physically harm human beings. Think of the steering or braking function of a car being compromised.
Besides that, damages can be of financial or legal nature. Credit card data can be stolen or the data protection rights of individuals can be violated.
While the protection of human life is universal across industries and cultures, legal implications might differ from country to country. Even financial damages are difficult to uniformly rate as high, medium or low as this heavily depends on the size and financial background of the corporation affected.
Other types of damages could defined depending on the respective system. E.g. could a degradation of the service level, reduced functionality or slower response times represent a damage category of its own.
The complex and highly subjective constellation of potential “negative consequence” make a standardardized security risk assessment very challenging.
This is especially problematic in an international and highly collaborative development environment like the automotive industry.
More challenges in security engineering arise from dependencies of security threats and security related countermeasures to other engineering and development aspects. Making a design secure changes the design. Hardware encryption modules are costly (economic impact), cryptographic measures use resources like processing power and bandwidth (economic and performance impact), security measures might contradict safety goals e.g. in a scenario where a locked door is safe but not secure and additional authentication processes have an impact on the user experience.
As a result, security engineering further raises the bar for effective, interdisciplinary collaboration methods and tools in the development process to model, analyse and evaluate security aspects.
What needs to happen in the area of security engineering in the years ahead?
Increase security awareness on all organizational levels
Managers, product owners, engineers and software developers need to be aware of the safety, legal and financial implications of security design. Security is not optional but core to any successful business.
Close regulatory gaps und minimize legal uncertainties
Regulatory bodies including IEC/ISO the EU and individual countries have to introduce norms and laws that govern the security engineering process. Similar to ISO 26262 for automotive functional safety the legal framework does not have to dictate methods and tools but define work products and documents required in the various phases of the development process.
This will not make the complexity of the security engineering process disappear but it will create a framework for organizations to optimize the process, define roles and produce the type documentation expected from a regulatory and legal perspective.
As an example, ISO/SAE 21434 is going to define a cybersecurity engineeringa framework for road vehicles. However, the first version is only expected to be released in the first half of 2020.
Integrate security engineers in the development process
Regardless of any norms and laws and the time of their availability, security related engineering tasks are complex and require know-how and experience. They also require interdisciplinary exchange across department boundaries. Companies need to acknowledge this by hiring and training security experts as an integral part of their development process. At the same time the process and the respective responsibilities have to be adjusted in order to ensure a “secure development process by design”.
Review existing methods and tooling landscape
In line with the expected regulatory frameworks and the defined roles and the responsibilities of the security engineers, methods and tools have to be reviewed. The following aspects can be be taken into consideration:
- Ability to flexibly model and analyse the system under development including all relevant security aspects (security goals, damage potentials, attack vectors, countermeasures etc.)
- Provide interfaces to integrate the security analysis in existing engineering toolchains
- Flexibility to adjust to upcoming changes introduced by regulations or improved best practice approaches
- Degree of automation and level of “intelligent tool support” in the areas of modeling and analysis
- Support of existing or expected regulatory capabilities including tracing, audit safe documentation and logging.
Jointly with Fraunhofer Institute for Applied and Integrated Security AISEC, itemis develops an architecture-based cyber security analysis solution for Automotive, IoT and Industry 4.0.
Send an email to security-analyst@itemis.de and get the latest information on the security-analysis solutions provided by itemis or leave us a comment!

Comments